Ashley is Awarded COMPTIA A+ Certification
 Breaking news! Ashley has passed her CompTIA A+ Certification exam! Congratulations from Tech Lab on your achievement! You’ve earned it.
Breaking news! Ashley has passed her CompTIA A+ Certification exam! Congratulations from Tech Lab on your achievement! You’ve earned it.
 Breaking news! Ashley has passed her CompTIA A+ Certification exam! Congratulations from Tech Lab on your achievement! You’ve earned it.
Breaking news! Ashley has passed her CompTIA A+ Certification exam! Congratulations from Tech Lab on your achievement! You’ve earned it.

Old Antenna Relay Circuit Board along side the replacement printed circuit board.
I have had an interest in electronics since I was small. I took an electronics course in High School and built a short wave radio receiver. Unfortunately we never got it to work correctly, my teacher reviewed the circuit and it appeared correct, but never worked. It sparked a desire in me to know more about the technologies that fuel many of the modern marvels we use in passing every day. I was amazed at how a simple concept like a short wave radio, could be so finicky!
Right around that same time, two of my friends, Jim and Mike, got me interested in Amateur Radio. It was $5 to pass a test and be able to talk to anyone who happened to be listening. I studied and passed the written exam along with passing the 5 words per minute morse code test. Don’t ask me to communicate with morse code today, I haven’t kept it up. What I did keep up, were years of connecting with others who also passed their Amateur Radio exams. I’ve spent many hours working with engineers who share the same interest in Radio Communication. From satellite dish receivers, to digital modes, and raspberry pi mini computers, there are a lot of technologies in use by the Amateur Radio community!
NASA also happens to partner with a non-profit program called ARISS (Amateur Radio on the International Space Station – ariss.org). It is a STEM outreach program to inspire kids who are learning Science, Technology, Engineering, and Math to pursue more of it. When a local Amateur Radio club and a local school submit an application together, if approved, NASA will schedule a day for the students to talk with the ISS directly, over the radio. Our radio station has antennas that are computer controlled and will “beam” the signal straight to the ISS as it passes overhead. The computer controls several motors on the antenna which move ever-so-slowly to track the ISS. The pass over us lasts about 15 minutes. Once the space station passes beyond the horizon, we lose contact, so it is a very brief window to speak directly with them.
Via more modern technologies, we have internet access on the space station too, and so, students can also ask their questions through the internet. Our method is a little more “old-school” but is still widely used in the space program. For example, when sending commands to a robot on Mars, the transmission must be aimed and timed appropriately so a satellite in Mars Orbit can receive the signal, and re-transmit it to the Mars surface, and thus to the rover that’s roaming around on the ground. These commands take 7-10 minutes each way! If you think our internet can be slow sometimes, try waiting 20 minutes round trip to see if a Mars rover even responded! There are a whole network of satellites around Mars in orbit, which receive and re-transmit signals to other Mars satellites, transmitting around the planet, eventually down to the ground, and then back up from the ground, and back to Earth again.
I’m a member of the Milwaukee Radio Amateur Club, one of the oldest clubs in the United States, and our club decided to sponsor our team. So for the last 3 years, a few of our members (retired and not-so-retired engineers) decided to build this radio station that would track the International Space Station and allow us to talk to the astronauts.
In building the radio station to talk to the ISS, we all had to exchange knowledge of radio and engineering. Ted worked for Rockwell Automation for many years as a facility engineer. His job was to lay out the floor plans for the projects the company would implement. He was extremely skilled at engineering things to fit in a restricted space, and thus our team ended up with a collapsible and fully transportable structure. When it is fully assembled it easily takes up the space of a small building, but also fits into a van when not in use. Ted also helped us understand how The Doppler Effect changes the radio signals whether the ISS is approaching or moving away from our position. Dean brought us some mechanical engineering skills. He was instrumental in rebuilding the motors for the rotor. The motors were straining and grinding pretty bad from years of rust and dirt build-up. Now the two motors spin freely thanks to his handy-work. He also built and assembled the aluminum backup antenna structure that NASA requires. I handled producing electronics and setting up the computer and control software. A few others helped out along the way, my friend Chris knows how to prototype circuit boards so the two of us actually removed two old rusted circuit boards from the 40 year old antennas, traced them with a micrometer, reproduced the boards in the computer, then remanufactured the two circuit boards as if they were brand new. Special thanks to Ham Radio Outlet for the antenna donation to our club and the space to work in the warehouse!
Part of the difficulty of this project was planning ahead. We only met once every month for a very short time, so planning was a large key to our success. We would talk briefly at the beginning of our work day about what had happened at the previous meeting and any work we put in between then and now. Then we would review our plans for that day for making progress on the project. Do the work. Then review what needed preparation for next time, things like ordering or picking up any new parts. Continuous communication was instrumental in the success of our group.
Today we have a radio station that is a multi-purpose tool beyond ISS communication. We can teach others about Amateur Radio and demonstrate how it works. We can definitely communicate with astronauts on the ISS. We can perform a technique called “moon bounce” (and it is exactly what you think), where we point the antenna at the moon, and the moon bounces the signal back to someone half way around our planet, then they do the same and the transmission bounces back to us for 2-way communication. We can point the antennas at satellites in orbit which also re-transmit signals over long distances. Then finally if conditions are good, we can point the antenna at the horizon and communicate directly with other ground stations upwards of 700 miles away (atmospheric conditions do need to be stellar for long distance ground communication to work).
I started this project with the idea that I wanted to build my own satellite station and learn how to provide ground to orbit communication. Now I can! Our team completed the radio station on March 4, 2022. I’m pretty excited about this accomplishment! If you would like to learn more about the projects I’m involved in, feel free to shoot us a contact. I look forward to meeting you!
Next time I’ll post about how we use Amateur Radio to track and communicate with Greyhound Buses for Irish Fest.
Stay Tuned!
 |
 |
 |
 |
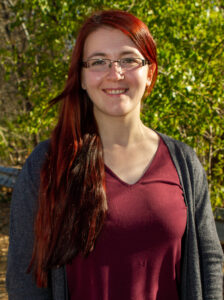
Like many people I was unsure what I wanted to do with my life upon leaving high school. After taking a year off I decided to follow in the footsteps of some of my family members and work with technology. It seemed a good way to ensure I could not only pay my bills but enjoy what I do on a day-to-day basis. Upon going to college, I faced some difficulties with the first school I attended telling me the program I wanted to join didn’t exist and the second school shutting down with my credits not being transferable. For me, third time really was the charm, and in 2017 I was able to go back for the degree I wanted. Thanks to the wonderful teachers and staff I had access to more resources than ever before and was able to get help with signing up for classes and financial aid. Since I was working full time and attending school part time, I was still taking classes when covid first shut everything down. I was working and attending classes remotely which made it difficult for me to concentrate and get things done on time. Plus, not being in the same room as my teachers made it more difficult to schedule time to meet with them to get answers to the questions I had. Thankfully, in the spring of 2021 I was able to graduate with honors and begin looking for a permanent position in my field. That fall I got a job at Tech Lab and began the next leg of my journey. Now I get to go to a job I enjoy and spend my time working in an ever-evolving field that will allow me to continue learning for the rest of my life.
Throughout human history there have been many wonderful and life changing inventions that shape the way we live today. Since today is St. Patrick’s Day, we will talk about 10 that have come from Ireland and the Irish in the last few centuries. The following list is in chronological order.
Robert discovered that the volume of a gas decreases when you increase the pressure and vice versa. This was named Boyle’s law. This is important because it explains how gasses behave therefore further explaining how the world around us works. On top of that he came up with a definition for elements that we now use to populate the periodic table. These discoveries where shaped how scientist view and interact with the world around them even now.
When a Cholera outbreak happened, he started looking at the blood of those infected and realized they were lacking salt and water. He found that giving the patient fluids through an IV helped and we still use this treatment today. This was a big deal because it was highly contagious and could cause extreme dehydration and death. To make things even more interesting this was before the invention of the hypodermic needle.
 When the induction coil was invented, it was able to produce more energy than other documented sources at the time. It produced intermittent high-voltage current from a low-voltage supply. In fact, while Nicholas thought it like an electromagnetic battery it was the world’s first transformer. While it isn’t as widely used as it once was, they can still be found in internal combustion engines and physics classrooms.
When the induction coil was invented, it was able to produce more energy than other documented sources at the time. It produced intermittent high-voltage current from a low-voltage supply. In fact, while Nicholas thought it like an electromagnetic battery it was the world’s first transformer. While it isn’t as widely used as it once was, they can still be found in internal combustion engines and physics classrooms.
 The first recorded hypodermic injection happened on June 3rd, 1844. Sadly, the invention is more commonly attributed to Alexander Wood in 1853. Even so, this was a monumental moment in medical history. Francis was trying to treat a woman with extreme pain around her eye and face but ingesting the medication didn’t work. He decided to attempt to place it under her skin near the area. This was the first time a local anesthetic was ever used. This invention used gravity to get the medication where it needed to go so there where some limits, but it paved the way for modern day syringes that can push fluids directly into the blood stream.
The first recorded hypodermic injection happened on June 3rd, 1844. Sadly, the invention is more commonly attributed to Alexander Wood in 1853. Even so, this was a monumental moment in medical history. Francis was trying to treat a woman with extreme pain around her eye and face but ingesting the medication didn’t work. He decided to attempt to place it under her skin near the area. This was the first time a local anesthetic was ever used. This invention used gravity to get the medication where it needed to go so there where some limits, but it paved the way for modern day syringes that can push fluids directly into the blood stream.
 While stethoscopes themselves existed before this, they were not as convenient or easy to use. They used to be a piece of metal the doctor would place on the chest and then had to place his ear against. Thanks to Arthur now doctors didn’t have to bend down as far and had more of a range of motion when trying to check different areas. The reason Arthur was able to create this invention was because of the introduction of Malaysian rubber tubbing. Sadly, the next year George Camman created a stethoscope with the same design in New York and failed to attribute the invention to Arthur which displeased that latter greatly.
While stethoscopes themselves existed before this, they were not as convenient or easy to use. They used to be a piece of metal the doctor would place on the chest and then had to place his ear against. Thanks to Arthur now doctors didn’t have to bend down as far and had more of a range of motion when trying to check different areas. The reason Arthur was able to create this invention was because of the introduction of Malaysian rubber tubbing. Sadly, the next year George Camman created a stethoscope with the same design in New York and failed to attribute the invention to Arthur which displeased that latter greatly.
 Charles used his invention to power an electrical generator that he designed which made cheap and plentiful energy possible. Not only did this change the way people viewed electricity but it also revolutionized marine transport. With this method ships could move faster than ever before. Today’s turbogenerators which provide most of the world’s electricity use some of the same concepts as this earlier model and wouldn’t be possible without it.
Charles used his invention to power an electrical generator that he designed which made cheap and plentiful energy possible. Not only did this change the way people viewed electricity but it also revolutionized marine transport. With this method ships could move faster than ever before. Today’s turbogenerators which provide most of the world’s electricity use some of the same concepts as this earlier model and wouldn’t be possible without it.
 Submarine technology had been in the works for many years before John Holland came around, but none had been quite successful. Many required humans to power them or didn’t fully submerge. After John immigrated to New York he broke his leg which gave him significant time to work in his designs. He combined electric motors and gasoline engines and created the first submarine to travel and considerable distance. In his later years he would also invent a device that allowed sailors to escape from damaged submarines, which would save many lives.
Submarine technology had been in the works for many years before John Holland came around, but none had been quite successful. Many required humans to power them or didn’t fully submerge. After John immigrated to New York he broke his leg which gave him significant time to work in his designs. He combined electric motors and gasoline engines and created the first submarine to travel and considerable distance. In his later years he would also invent a device that allowed sailors to escape from damaged submarines, which would save many lives.
Once people discovered that there where invisible waves affecting the world around us our understating of things greatly shifted. Marie and Pierre Curie where the ones that discovered radioactive materials could not only cause cancer but burn and maybe destroy it but the methods they used where dangerous to both the doctor and the patient and unreliable. John decided to look for an alternative for these reasons as well as it being extremely expensive to obtain the smallest amount of radium. After he learned that the radioactive gas from radium could be collected and injected directly into the cancerous growth everyone began using the new method. Not only was it more reliable and safer, but since the same sample of radium could be used for multiple doses, it was cheaper as well. To this day anyone who has received injection-based chemotherapy can have John Joly to thank.
James’s battery changed mainly the train industry in his time but in modern times we use his batteries for electric garden equipment and deep cycle marine applications. His batteries where not only rechargeable but allowed for quick charges and discharges. This translated to the train being able to accelerate faster, allowing them to break more with out hurting the arrival time. Making travel faster and safter. The trains that he built could travel at least 80 miles on a single charge and ran for 17 years.
 During the 60s cardiac problems seemed to be on the rise with people dyeing before they even made it to the hospital. Frank figured the reason was that they needed to be taken care of before they got to the hospital to minimize complications and increase the probability of survival. So, he created a Defibrillator that could be powered by car batteries so that when first responders got to the scene, they could shock the patient before bringing them to the hospital. Once it was clear this was effective, he would install them in ambulances so that they would always have one with them. He would take things a step further and design an automated external defibrillator so that general members of the public could safely use it. The automated defibrillator would only shock the patient if it detected a cardiac event thus preventing possible injury to someone who had merely fainted. At this point this design has save innumerable lives across the globe.
During the 60s cardiac problems seemed to be on the rise with people dyeing before they even made it to the hospital. Frank figured the reason was that they needed to be taken care of before they got to the hospital to minimize complications and increase the probability of survival. So, he created a Defibrillator that could be powered by car batteries so that when first responders got to the scene, they could shock the patient before bringing them to the hospital. Once it was clear this was effective, he would install them in ambulances so that they would always have one with them. He would take things a step further and design an automated external defibrillator so that general members of the public could safely use it. The automated defibrillator would only shock the patient if it detected a cardiac event thus preventing possible injury to someone who had merely fainted. At this point this design has save innumerable lives across the globe.
These are only some of the wonderful things that the Irish have added to our world. If you’re interested in learning more about Irish culture, you could attend Irish fest in August. There is a link to the site down below.
 What IT means to me and why I chose it?
What IT means to me and why I chose it?For me, IT came into my life at a time I had needed it most. It saved me. I discovered my passion for IT while working at a job that I was not happy at. That is where I became the go-to girl for tech questions although it was not my position. Soon I found myself more curious and decided I had to take the risk and go for it. The choice left me with feelings of uncertainty, and I questioned myself if I had made the right decision. Little did I know, it was the best choice I have made for myself and my future. Today I wake up every day happy and excited to go to work. And it’s true what they say; if you do what you love you will never work a day in your life.
Tech Lab has had some recent staff changes.
In April, Michelle left Tech Lab after two years of service. We thank her for her dedication and helping to move our company forward. She has been greatly missed and we wish her the best in her future endeavors.
It is with a heavy heart that Tech Lab says farewell to Amanda. She has been with the company almost 9 years and has determined that it is time to make a change. She has invested countless hours in helping Tech Lab establish itself as a premiere technology company in the Milwaukee area and we are sad to see her leave. We wish Amanda the best as she pursues her other passion as a Mary Kay consultant! Thank you for 9 years of service and dedication to our growing company!
Gregg was recently hired as the new Operations Manager. He comes with experience in operations at a previous IT company. He is a great addition and will help us move into the next chapter at Tech Lab.
What is smart home automation? Smart home automation uses technology in your house to automate tasks. As part of how that is set up, you can also control remotely whatever technology is hooked up to it.
How does it work? Some of the devices connect directly to the Internet, and some of the devices are controlled with infrared or radio frequencies over WiFi. In this way, you can use a tablet or a phone or your voice to control all the devices wired into your smart home.
What kinds of devices can I hook up to my smart home? Many appliances have now have smart features integrated or you can purchase devices to integrated them. Ideas include: a faucet in a sink, a bathtub, thermostat, oven, microwave, blinds, washers & dryers, garage door, doorbell, lights, door locks, phones, security systems, entertainment systems, sound systems, etc.
If it has a remote, it can be hooked up. If it plugs into the wall, it can be hooked up. Nonetheless, you will often have more options and simpler controls if you purchase smart devices.
For example, if you have a fan that you plug into the wall with a smart plug, the most that the plug is going to be able to do is turn the fan off and on, even if you have different speed options on the fan. On the other hand, if you buy a smart fan, you can integrate the fan with the rest of your climate control system, in addition to being able to control the speed.
What can Tech Lab do for me?
At Tech Lab, we specialize in interconnecting all of these devices. Many different companies provide different products for smart home automation. No one company provides all of the options that are out there. Each has a different interface that we consolidate into one device.
We are also an IT company that specializes in network environments. When you have a smart home, you have an in-home Internet network with many smart devices hooked up to it. That can very quickly slow your Internet down to the point that you have a lag when you want something done. It can also be a tempting target for hackers, and we provide security and monitoring to prevent bottlenecks and attacks. If you have these devices installed but are having problems or want more security call Tech Lab at 414-208-4682.
We can install many of these devices, but for some, such as the smart bathroom and the smart kitchen, you will want a specialist to install them. Contact us at Tech Lab to discuss your project to help determine the best plan of action for you at 414-208-4682.
So many options are available to you just to use the internet. Which browser should I use? Do I need an adblocker? What are cookies?
First of all, what browser do you choose? Google Chrome is the most secure and Tech Lab’s recommended browser. Mozilla Firefox and Safari are other reasonably secure options. Microsoft Edge and Internet Explorer are less secure. That being said, if you can’t get to a site on Chrome, try Edge or Internet Explorer, though beware because the site is probably sketchy.
Additionally, in each browser you can add extensions to make your Internet experience safer:
Your browser itself will warn you sometimes of the security of a site. Sometimes, even without any extensions, it will recommend that you not go to the website. This is your computer trying to protect you. Sometimes it will tell you that a site is not secure. If it tells you that a site is not secure, we recommend not putting in any important information like passwords or bank information. You will also know if a website is secure if you see the lock icon in the left corner of your address bar.
Many browsers will ask to save your information, including your email and address, your credit card information, and passwords. This prevents you from having to type in and remember all this information. This can be a great way to remember a lot of different passwords, but we recommend having another copy somewhere of the passwords as well. That way, if you lose your device, you still have all your passwords. You also need to be sure that if you are saving your credit card information you are using a secure website which you can trust.
A new feature that has been recently added to many browsers is syncing. This feature allows you to see the same websites you were surfing on one device to show up exactly the same on another device like your phone or tablet. If you have saved any passwords or credit card information on that browser, they will also show up on that other device. If you take advantage of this feature (e.g., to save passwords or financial information), make sure that your account has a password on it that you don’t use anywhere else.
If you are experiencing problems connecting to certain websites you can also clear your browsing history, temporary Internet files, saved passwords, and cookies. Deleting cookies prevents companies’ websites from tracking you. You can find these settings in Chrome under More Tools. Be aware that when you delete these items they are gone forever and you cannot get this information back without accessing it another way. If you are not sure how to clear this data, call Tech Lab to help at 414-208-4682.
Everyone has been there. You are working on a document and then either you forget to save it or can’t find where you saved it to. What do you then? Here are some ideas to consider as you look for your file.
Still can’t find what you need? TL can find it for you. Call us at 414-208-4682 or contact us here and a technician will reach out to you.
Tech Lab strives to give back to the community. Several of our staff enjoy working with kids as well. When a partnership formed with Make-A-Wish Wisconsin, Tech Lab was able to fulfill a teenager’s wish which allowed us to achieve both of these goals.
On June 18, Tech Lab employees started their morning with the final preparations to help fulfill a wish of a teenager. Balloons, banners, and spirals were hung and canopy tents were put up in the back. Computer parts were put on display. After a couple of months of planning and purchasing equipment, everything came down to this day.
Nicolas had a wish to be able to build his own computer and Tech Lab worked with him to accomplish this dream of his in partnership with Make-A-Wish Wisconsin.
Just after 10am, Nicolas and his family came to our office. He was greeted by Make-A-Wish volunteers and staff and Tech Lab’s staff. Additionally, three news crews came to capture Nicolas’ big day. After his arrival, Nicolas enjoyed his favorite dessert of a homemade pumpkin pie. He then looked closer at all the components of his new computer and opened them. Nicolas and his family also spoke to the news crews. Finally, he was able to work with Coty to build his own computer from scratch. Nicolas helped put in the graphics card, processor, and other components. Just after lunch, the computer was built and then Windows was installed along with all of the accessories. After 5 hours of working at Tech Lab’s office, everything was packed up and the family went home. Roger ensured everything was set for Nicolas in his home with his brand new computer and completed the fulfillment of his dream. Nicolas told our staff the first game he would play would be Fortnight.
This day was a very special experience for all of our staff. We were honored to give back to the local community in such a way that directly impacted a family and Nicolas’s future goals. Coty said he enjoyed sharing the same interests as Nicolas. He also enjoyed “facilitating an experience that your average person doesn’t get to experience.” Tech Lab’s staff was excited to bring joy to Nicolas on his special day and looks forward to the joy he will bring to others.
Tech Lab plans to partner with Make-A-Wish in the future and fulfill the dreams of more children. If you would like to help fulfill a child’s wish Make-A-Wish Wisconsin is always looking for donations and has a Walk event coming up in August as well.
If you would like to experience building your own computer, this experience is open to the public. Anyone can book one of our technicians to help them build their own computer. Tech Lab will purchase the parts based on the type of computer you would like to have. After the parts arrive, you spend half a day with our technician to learn how computer parts go together and how a computer works. At the end of the half day, you take your brand new computer home. You also have the option of having a technician come to your home afterwards to fully customize your computer with your programs and peripherals. To learn more information about TechKids, click here.
If you didn’t catch the news stories live, you can view them here.